Our Services
Take Your Business to Next Level
Our skillful and highly competent team of IT specialists will help you in creating an innovative and effective online presence for your company. Let’s explore our services.
Want to Drive More Traffic To Your Business?
In today’s world, the digital presence of a business is the most important thing for customers. It generally shows how professional and reliable your work is. As you may know, the first impression is always the last impression. Therefore, your brand’s face should look presentable and a customer should have an indulging experience with it so that it leaves a thoughtful impact forever.
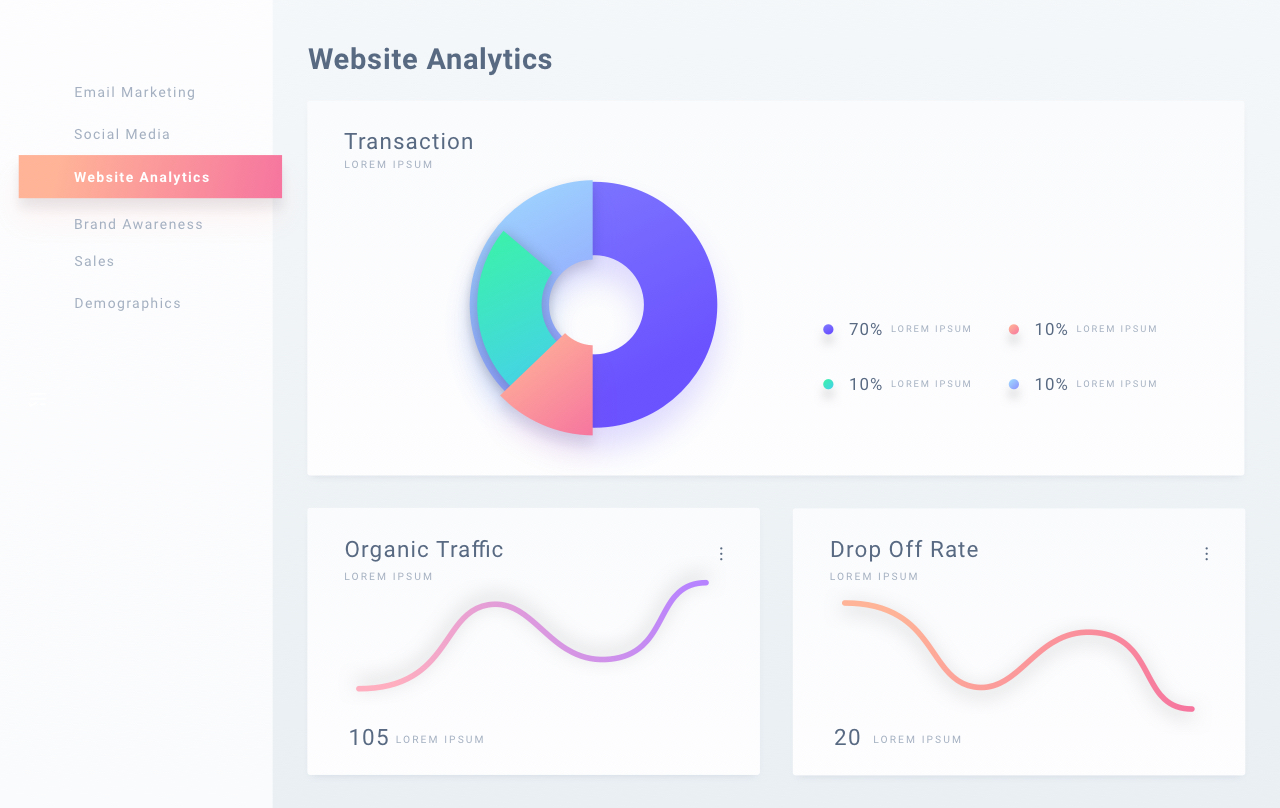
Our skillful team aims to provide you with a sound, secure and reliable bundle of dedicated web and IT services packed with the latest trends and technologies. We will understand and transfer your business ideas and requirements into a custom and secure web solution that will meet the top quality standards.
Our vast services include solutions to all your worries. Be it managing any IT issue like Wi-Fi or printers giving errors, or system’s security scan and health assessment. We also give quarterly cyber security seminars in corporate offices to teach the employees about the importance of browser safety, password health and other necessary security measures. You can also put request for email and cloud migration and management. View our services down below.
Owning a Business Can Be Overwhelming. The Good News Is, We Are Here to Solve Your IT Issues.
Website Development
Web Development is the process of building and maintaining websites that are hosted via intranet or the internet. It gives a digital presence to your brand.
Email Management & Migration
Email migration is the process of moving from one email provider to another. It also involves managing emails, contacts, and other data that is transferred between email services.
Up-to-date Systems & Software
Updating the system and software regularly helps in improving system performance, program stability, fixing bugs and enhancing system utilities and compatibility.
Search Engine Optimization
SEO helps to improve the quality and quantity of website traffic to a website or a web page from various search engines. It targets unpaid traffic rather than direct traffic or paid traffic.
Manage IT Issues
This covers identifying, analyzing, and resolving IT problems which can involve product failures, software defects, PC and Printers disconnection, and more.
Team Training on Cyber Security
This training focuses on educating staff about potential IT risks and vulnerabilities so that they can identify any security threats that could happen when working online and with shared systems.
System Backup Validations
Backups are very helpful in case of any cyber attack or security breach. These validations are to check and verify the success of an information backup of a database or other system files.
Cyber Security Assessment
A cybersecurity risk assessment is the identification of the various information assets that could be affected by a cyber attack and the various risks that could affect those assets.
Cloud Migration and Management
Cloud migration and management is the process of transferring and maintaining data, applications or other business elements from one cloud computing environment to another.
Setting Up the New Devices
Setting up new devices can be an extra task on top of other daily duties. But, don’t sweat it. We’re here to help with you guides to set up the new gadgets and devices.
Online Marketing Support
This support consists of developing and deploying effective marketing strategies to promote products and services online. It will ensure that your brand connects with your consumer.
Company IT Policies
There can be various company IT policies including security incident response policy, VPN usage policy, data encryption policy, identity theft protection policy, user privilege policy and many others.
New Employee IT Onboarding
This process can help the new employees in familiarizing themselves with hardware and software, setting up accounts, learning and following security guidelines, etc.